Preventing GBP Spam: 2025 Ultimate Defense Guide
Master preventing GBP spam with our 2025 ultimate defense guide. Learn proven strategies to protect your Google Business Profile from scams and fake listings.

William Turner
Founder of William & Friends
Oct 30, 2025
10
The digital landscape has become a battleground for local businesses, with Google Business Profile spam attacks reaching unprecedented levels. Your business's online reputation, local search visibility, and revenue stream hang in the balance every single day. What started as occasional fake reviews has evolved into sophisticated, coordinated attacks, ownership hijacks, AI-powered strikes that can erase you from the search and devastate businesses within hours.
Google Business Profile suspensions surged by over 80% between Q1 2023 and Q2 2024, creating chaos for legitimate businesses caught in the crossfire. Google's response has been equally dramatic, with the platform removing over 115 million policy-violating reviews and disabling 200,000 user accounts in 2023 alone. The stakes have never been higher, and traditional "set it and forget it" approaches to profile management are no longer sufficient. You can get proactive defense with our Google Business Profile management and protection.
This guide arms you with the latest defense strategies, recovery protocols, how to harden your profile, and proactive measures needed to protect your business in 2025's hostile digital environment.
TL;DR
Treat your Google Business Profile like a high-risk asset. Lock ownership with two backup owners and 2FA on every user, run quarterly access hygiene, and keep categories, name, phone, website, and service areas clean and consistent. Monitor for tampering, build a review defense routine, and keep your website secure to avoid collateral suspensions. When attacks happen, act fast: revert edits, remove rogue users, submit a documented appeal with signage and proof, restore trust signals, and measure recovery by calls, reinstatement time, review velocity, and rating trend.
Key Points |
|---|
|
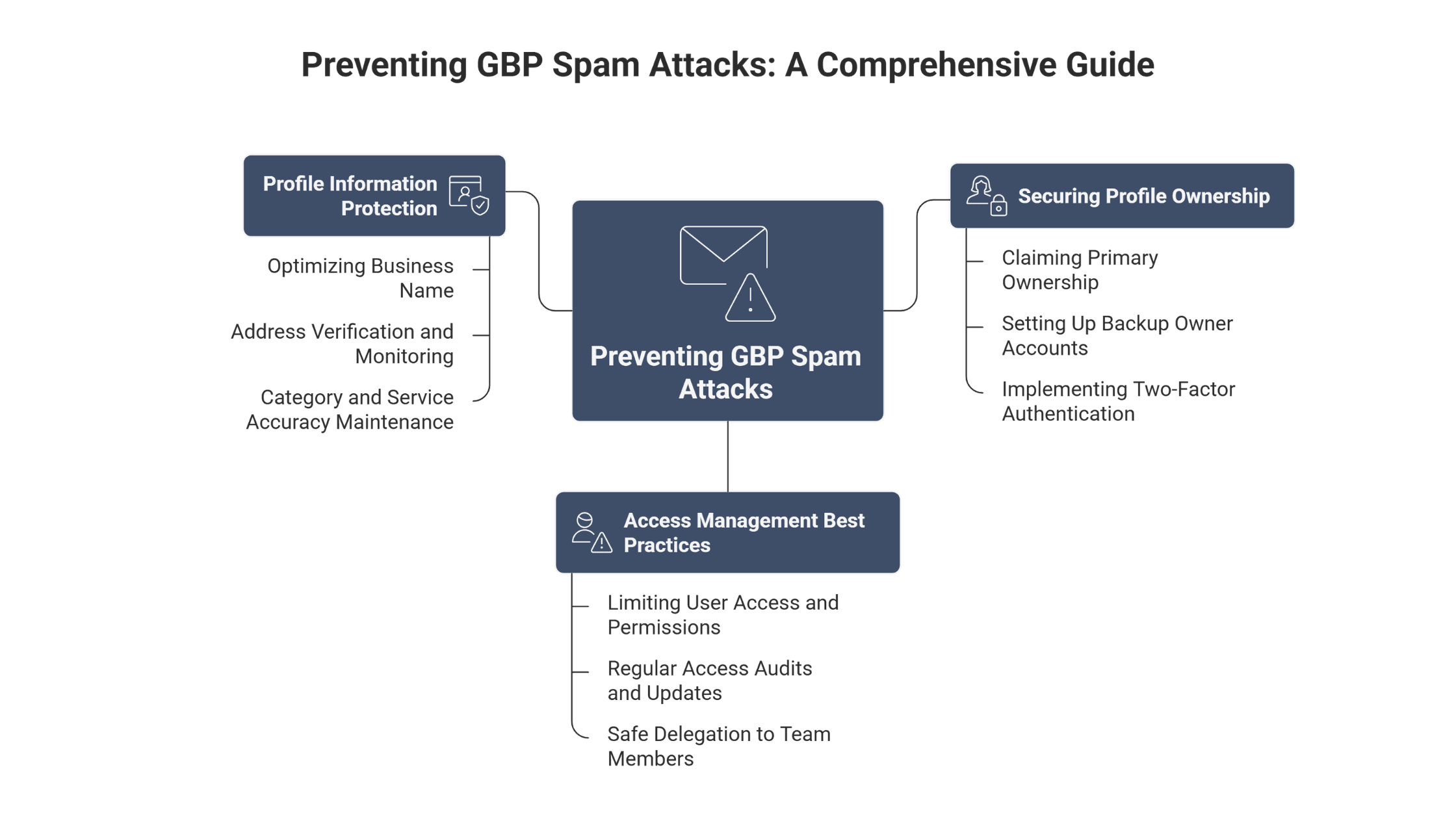
Complete Guide to Preventing GBP Spam Attacks
Securing Your Profile Ownership
Claiming Primary Ownership Before Scammers Do
Speed determines survival in the GBP ownership race. Unclaimed profiles represent easy targets for attackers who can seize control, lock out rightful owners, and begin manipulating business information within hours. The claiming process takes minutes but provides the foundational security layer that prevents unauthorized access.
Google's 2025 verification requirements have become more stringent, with stricter business verification now requiring additional documentation. Video verification serves as the primary authentication method for new claims and major changes, involving recording your business exterior with visible signage, interior spaces, and proof of operational control like unlocking doors or accessing business-only areas.
Permanent signs are now required—temporary signs such as banners or printouts no longer meet Google's updated requirements for verifying a business location. This change eliminates a common loophole that spammers previously exploited to verify fake locations.
Not sure your verification package will pass? Ask our team to review your profile before you submit.
Setting Up Backup Owner Accounts
Single points of failure create unnecessary vulnerability in GBP management. Establishing backup owner accounts ensures business continuity when primary owners leave organizations, lose access credentials, or face targeted account attacks. Multiple trusted owners reduce lockout risks and facilitate smoother management transitions during crises.
The key lies in selecting backup owners with genuine business stakes rather than convenience. Former employees, contractors, or third parties without ongoing business relationships should never maintain owner-level access. Each backup owner must implement identical security protocols, including two-factor authentication and secure password management.
Backup accounts prove essential during recovery scenarios when primary accounts face suspension or compromise. Having verified alternatives allows immediate response to attacks without waiting for lengthy Google support processes that can extend business disruption for weeks.
Implementing Two-Factor Authentication
Password-only protection crumbles against modern attack vectors. Two-factor authentication creates a critical security barrier that prevents unauthorized access even when passwords are compromised through phishing, data breaches, or credential stuffing attacks.
Google's implementation requires authentication codes from mobile devices or authenticator apps, making account takeovers significantly more difficult for remote attackers. This protection extends beyond GBP to encompass the entire Google ecosystem, protecting associated Gmail accounts, Google Ads, and other connected business tools.
All team members with GBP access must maintain consistent 2FA standards. The security chain breaks at its weakest link, and a single unprotected account can provide attackers with the foothold needed to compromise entire business profiles.
Access Management Best Practices
Limiting User Access and Permissions
The principle of least privilege applies directly to GBP management. Granting access only to individuals who require it for their specific roles minimizes potential attack vectors while limiting damage scope if accounts become compromised. Google provides three permission levels: Primary Owner, Owner, and Manager, each with distinct capabilities and restrictions.
Regular permission audits identify and eliminate unnecessary access before it becomes a liability. Documentation of all access grants, changes, and removals creates accountability trails that prove invaluable during security investigations or compliance reviews.
Business authenticity checks now flag discrepancies in address details, use of PO boxes or mail services, and shared office spaces. These factors are more likely to trigger flagging or suspensions under 2025's enhanced verification standards.
Regular Access Audits and Updates
Static access management invites security breaches. Quarterly audits should examine all user accounts, verify current employment status, confirm ongoing business need, and remove outdated permissions. Former employees, changed contractors, and concluded business relationships represent immediate security risks that require prompt attention.
Access logs reveal unusual activity patterns that may indicate compromised accounts or unauthorized usage. Monitoring login locations, timing, and modification patterns helps identify security breaches early in their development when mitigation remains possible.
Linked account problems can cascade—if a manager's Google account faces suspension, associated GBP profiles can be affected as well. This interconnected risk makes comprehensive account security essential for all team members with profile access.
We run quarterly permission audits as part of our managed services.
Safe Delegation to Team Members
Delegation without training creates unnecessary vulnerability. Team members receiving GBP access need clear guidelines on security best practices, responsibilities, and procedures for recognizing potential scam attempts. This education prevents well-intentioned mistakes that could compromise business profiles.
Official channels must be used for all user additions and removals. Informal access sharing, password distribution, or credential borrowing undermines security protocols and creates untrackable access points that attackers can exploit. Google's formal user management system provides audit trails and controlled permissions that informal arrangements cannot match.
Documentation of delegation decisions, training completion, and ongoing responsibilities creates accountability structures that improve security compliance and provide evidence during any future investigations or recovery efforts.
Profile Information Protection
Optimizing Business Name to Prevent Keyword Stuffing
Your business name should reflect reality, not search optimization fantasies. Using your actual business name as it appears on signage, legal documents, and official registrations maintains Google policy compliance while preventing suspension risks associated with keyword manipulation attempts.
Business names with unnatural keyword stuffing are now automatically flagged by Google's enhanced AI detection systems. This enforcement has dramatically increased suspension rates for businesses attempting to game the system through naming manipulation.
Monitoring prevents unauthorized name changes that could indicate profile compromise or competitor interference. Attackers sometimes modify business names to include negative terms, competitor references, or spam keywords designed to damage reputation and search performance.
Address Verification and Monitoring
Address accuracy forms the foundation of local search credibility. Virtual offices, mail forwarding services, and residential addresses create policy violations that invite suspension while undermining customer trust. Your listed address must correspond to your actual business location with visible signage and operational presence.
Home-based businesses must hide their address unless customer visits are allowed, while online-only businesses cannot list their profiles as local. These 2025 policy clarifications eliminate previous gray areas that spammers exploited.
Discrepancies in business information across online profiles now trigger enhanced scrutiny. Mismatched phone numbers, addresses, or other contact details between your GBP and other platforms can result in suspension under Google's stricter consistency requirements.
Category and Service Accuracy Maintenance
Category selection impacts both search visibility and policy compliance. Choosing overly broad categories, irrelevant specializations, or prohibited classifications creates suspension risks while potentially misleading customers about your actual capabilities and offerings.
Bulk edits or excessive updates to category, name, and address now raise suspicion under Google's 2025 monitoring systems. Frequent changes suggest manipulation attempts and can trigger manual review or automatic suspension.
Regular category reviews ensure ongoing accuracy as your business evolves. Service expansions, specialization changes, or operational modifications may require category updates that maintain compliance while accurately representing current capabilities.
Identifying and Combating Different Types of GBP Spam
Competitor Spam Tactics
Fake Duplicate Listings
Duplicate listings represent one of the most damaging spam tactics targeting legitimate businesses. Multiple fake GBP listings for a well-known dental clinic in Toronto were created by automated bots, slightly altering business names to stuff keywords and manipulate rankings. These duplicates briefly outranked the legitimate business, diverting leads and causing a 35% drop in calls during the confusion period.
Detection requires vigilant monitoring of search results for your business name, services, and location combinations. Duplicates often use slight variations in business names, addresses, or phone numbers while copying legitimate photos, descriptions, and other content. Cross-referencing multiple search queries helps identify unauthorized copies before they establish ranking authority.
The retail sector has been particularly hard hit, with automated fake listings and review bombing campaigns targeting legitimate shops. These attacks resulted in up to 60% drops in foot traffic or click-to-call metrics during spam waves, demonstrating the immediate business impact of duplicate listing fraud.
Keyword Stuffing in Business Names
Business name manipulation has evolved beyond simple keyword addition to sophisticated ranking manipulation schemes. The legal industry has seen widespread keyword stuffing of legal service names, with fake attorneys using names like "Best Personal Injury Lawyer City 24/7" instead of legitimate business names to capture broad search queries.
These manipulated names violate Google's policies but often persist for weeks or months before removal, capturing valuable search traffic during their active periods. Real law firms were buried in local results, lost first-page visibility, or faced suspension due to association with mass spam in their industry cluster.
Multiple listings with the same phone number now automatically risk suspension under Google's 2025 enforcement protocols. This change targets a common spam tactic where single operators create dozens of fake listings using shared contact information.
Virtual Office and Fake Address Schemes
Virtual office spam has become increasingly sophisticated, with attackers using legitimate-appearing business addresses that provide no actual service presence. The healthcare sector has reported widespread fake clinics or practitioners in the same city using similar keywords, creating false local authority while avoiding operational overhead costs.
Detection requires investigation beyond simple address verification. Real businesses display visible signage, maintain operational hours, and provide actual services at their listed locations. Virtual office spam typically relies on mail forwarding services, shared office spaces, or residential addresses with no business presence.
Healthcare businesses have experienced loss of profile control, drops in legitimate appointment bookings, and patient confusion during these attacks. Recovery timeframes range from several days to several weeks to reinstate suspended or hijacked listings, with measurable lead loss during downtime.
Review-Based Spam and Extortion
Fake Negative Review Attacks
Coordinated negative review attacks represent one of the most immediately damaging spam tactics businesses face. A recent case in the pest control industry demonstrates the evolving sophistication of these attacks. A wave of fake 1-star reviews appeared, none from legitimate customers, dropping the company's rating from 5.0 to 4.7 overnight.
The attack escalated when the business owner received a WhatsApp message demanding $100 or threatening 35 more negative reviews. This classic review blackmail tactic combines immediate reputation damage with direct extortion pressure, creating urgent motivation for victims to comply with demands.
Recovery took approximately 4 days after flagging reviews, submitting evidence to Google, and maintaining persistent support tickets. The relatively quick resolution demonstrates that proper documentation and escalation procedures can effectively combat review extortion when handled correctly.
Review Blackmail and Extortion Schemes
Review extortion combines fake negative reviews with direct threats, creating immediate pressure for businesses to pay for attack cessation. These schemes exploit the visible impact of negative reviews on local search rankings and customer perceptions, making rapid payment seem like the most practical solution.
However, succumbing to extortion demands encourages repeat attacks while violating Google's policies regarding review manipulation. Documented cases show that businesses paying extortion fees often face escalated demands and repeated attacks as criminals identify profitable targets.
The proper response involves immediate documentation of threats, preservation of communication evidence, and formal reporting through appropriate channels. Google's AI moderation for reviews now automatically reviews new submissions for authenticity and spam signals, flagging suspicious or irrelevant feedback more effectively than previous systems.
Competitor Review Manipulation
Competitor-driven review manipulation encompasses both positive review inflation for attackers and negative review campaigns against targets. These coordinated efforts distort local search results while undermining the review ecosystem's credibility for all businesses.
Detection of fake or purchased reviews has improved significantly, with sudden influxes of positive reviews or obvious manipulation much more likely to trigger manual review or suspension. Google's enhanced detection capabilities mean traditional review manipulation tactics face higher failure rates.
Identification requires pattern analysis across multiple time periods and reviewer profiles. Legitimate reviews typically show diverse timing, varied language patterns, and reviewers with established Google account histories. Manipulated reviews often cluster in timing, use similar phrasing, or come from profiles with limited review history.
Profile Hijacking and Impersonation
Unauthorized Profile Claims
Profile hijacking through unauthorized ownership claims has become increasingly sophisticated, with attackers exploiting Google's verification processes to seize control of legitimate business profiles. These attacks often target unclaimed profiles or businesses with weak access management practices.
Roe Digital reported its own GBP was targeted, with attackers relocating the business pin to an irrelevant location and altering key details including address and phone numbers. This manipulation led to rapid decline in local rankings and visibility, leaving customers unable to locate or contact the business effectively.
The restaurant industry has faced similar challenges with profile tampering and fake takeover requests. Imposter calls and emails pretending to be "Google Support" request profile ownership transfer or change restaurant information to false data, causing legitimate establishments to lose bookings due to incorrect information.
Information Manipulation Attacks
Information manipulation represents a subtler but equally damaging attack vector where criminals modify business details to disrupt operations without triggering immediate suspension alerts. These changes often target contact information, business hours, website links, or service descriptions.
Security issues linked to business profiles such as compromised websites now lead to automatic suspension under Google's enhanced security protocols. This connection between web security and profile integrity means businesses must maintain comprehensive cybersecurity across all digital assets.
Detection timelines vary significantly based on monitoring frequency and change visibility. Contact information changes often generate immediate customer confusion, while subtle modifications to descriptions or categories may persist unnoticed for extended periods while undermining search performance and customer trust.
Service Area Expansion Fraud
Service area manipulation allows attackers to artificially expand coverage zones, appearing in search results for geographic areas where they provide no actual services. This tactic diverts customers from legitimate local providers while violating Google's service area policies.
The fraud typically involves gradual expansion of service radius settings or addition of illegitimate service locations that create false local presence. Customers discover the deception only after attempting to schedule services, leading to frustration and negative experiences that can damage entire industry reputations.
Legitimate businesses combat this fraud by maintaining accurate service area representations while reporting suspected violations through proper channels. Crackdowns on misleading business information mean profiles with fake locations, misleading names, duplicate listings, or false operating hours face significant visibility reduction and higher suspension risk.
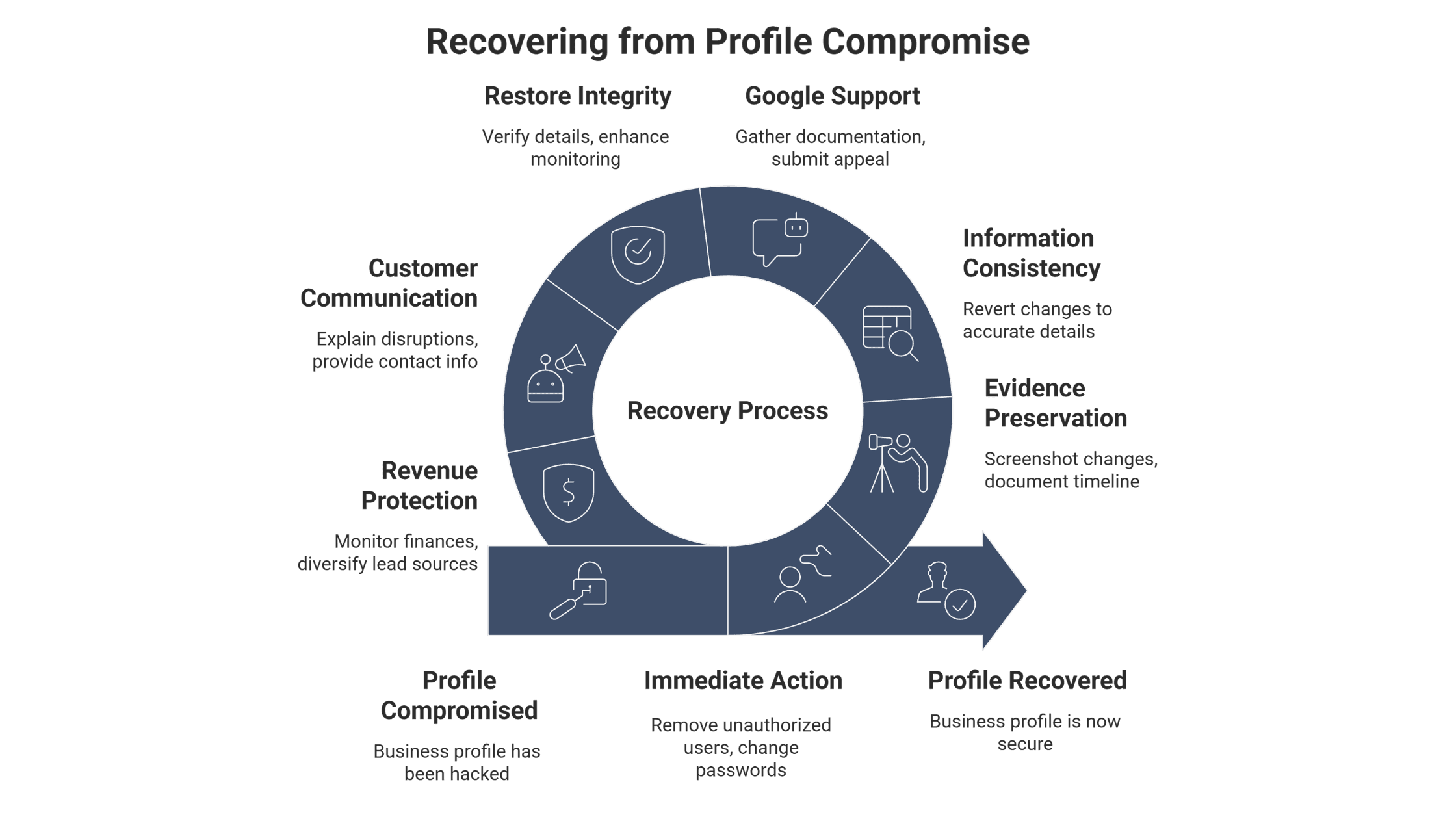
GBP Recovery and Damage Control
Signs Your Profile Has Been Compromised
Profile compromise symptoms often appear gradually, making early detection crucial for limiting damage scope. Unrecognized changes to business information such as name modifications, address alterations, or contact detail updates represent clear compromise indicators that require immediate investigation and response.
Login anomalies provide another critical warning system. Unusual access patterns, unfamiliar user additions, or unexpected permission changes indicate potential unauthorized access that could escalate into full profile takeover without prompt intervention.
Customer confusion often serves as the first external indicator of profile problems. Reports of incorrect information, inability to contact your business, or questions about services you don't provide suggest information manipulation that requires immediate attention and correction.
Step-by-Step Recovery Process
Immediate Action Items
Speed determines recovery success when dealing with profile compromise. First, remove any unauthorized users from your account access list while documenting their presence for potential investigation. Change all relevant passwords immediately, including Google accounts, associated email addresses, and any connected business tools.
Evidence preservation proves essential for both recovery efforts and potential legal action. Screenshot all unauthorized changes, preserve email communications, and document the timeline of discovery and response actions for submission to Google support or law enforcement if necessary.
Ensure all business information maintains consistency across platforms while reverting unauthorized changes to accurate business details. This consistency helps rebuild credibility signals that attackers may have disrupted through inconsistent information manipulation.
Working with Google Support
Google's 2025 recovery process emphasizes comprehensive documentation and single-case submission protocols. Gather comprehensive documentation including business license, tax certificate, recent utility bills, storefront and signage photos, video walkthroughs of your business location, and business registration paperwork before initiating contact.
The official appeal process requires precise information matching between submitted documentation and your business registration details. Upload all supporting evidence in clearly labeled formats while providing concise narratives explaining the situation and desired resolution.
Google typically replies within 3-7 business days for properly documented appeals, with most businesses seeing reinstatement within a few days to several weeks following proper documentation submission. Complex cases involving multiple violations or repeat offenses may require extended review periods and additional evidence.
Restoring Profile Integrity
Profile integrity restoration extends beyond simple information correction to encompass trust signal rebuilding and ongoing security implementation. Verify that all profile details accurately reflect current business operations while implementing enhanced monitoring systems to prevent future compromise.
Recovery measurement requires tracking key performance indicators including search ranking recovery, customer inquiry restoration, and review profile normalization. These metrics provide objective evidence of recovery progress while identifying any persistent issues requiring additional attention.
Frequent review responses and Q&A updates now boost profile ranking under Google's 2025 algorithm updates. Inactive profiles that rarely respond or engage see diminished visibility, making proactive engagement essential for maintaining strong local search performance.
Minimizing Business Impact
Customer Communication Strategies
Transparent communication builds customer trust during recovery periods while preventing confusion that could drive business to competitors. Proactive outreach through email, social media, and website updates should clearly explain any service disruptions while providing accurate contact information and service details.
Multiple communication channels ensure message delivery even when primary contact methods face disruption. Social media, email marketing, and direct website updates provide redundant pathways for reaching customers when phone systems or other contact methods experience problems.
Google's new WhatsApp integration allows businesses to connect WhatsApp to their profiles for instant customer communication, providing an additional channel for maintaining customer contact during profile recovery situations.
Revenue Protection Measures
Financial monitoring becomes critical during profile compromise recovery, as attackers sometimes attempt to access payment systems or redirect customer payments to fraudulent accounts. Review all business financial accounts for unauthorized transactions while implementing additional verification procedures for new payment processing.
Lead generation diversification reduces dependence on Google Business Profile visibility during recovery periods. Developing multiple traffic sources and marketing channels limits dependency on Google profiles while maintaining business flow during disruption periods.
Revenue tracking during recovery provides objective measurement of attack impact while identifying successful mitigation strategies. The documented experience that 61% of affected businesses experienced measurable declines in leads or calls during suspension and recovery periods makes comprehensive impact assessment essential for recovery planning.
Reputation Management During Recovery
Active reputation management during recovery prevents long-term damage that could persist after technical issues resolve. Promptly responding to reviews both during and after outages combined with updating customers via alternate channels helps restore and protect reputation during vulnerable periods.
Professional response to negative reviews generated during compromise periods demonstrates commitment to customer service while providing context for any service disruptions. Acknowledge legitimate concerns while clarifying any misinformation resulting from profile manipulation or system problems.
Reviews now support emojis and photos, displayed in story format for enhanced user engagement. These new features provide additional opportunities for authentic customer feedback while making fake reviews more detectable through their lack of genuine personal details.
William & Friends: Let Us Manage Your Google Business Profile So You Never Have to Worry
After reading about the complex web of threats targeting Google Business Profiles, you might feel overwhelmed by the constant vigilance required to protect your business. That's exactly why William & Friends specializes in comprehensive GBP management that removes this burden from your shoulders entirely.
Our team has witnessed firsthand how quickly GBP attacks can devastate local businesses. We've guided clients through profile suspensions, competitor attacks, and sophisticated impersonation schemes while developing the expertise needed to prevent these problems before they start. When you work with us, you're not just getting profile management—you're getting peace of mind.
William & Friends provides specialized Google Business Profile management services focused on optimizing visibility, preventing spam attacks, and building client credibility. Our expertise centers on maximizing local search presence for service-based businesses while proactively protecting against fraudulent activity that could damage your reputation or rankings.
Our comprehensive approach includes advanced monitoring tools that detect suspicious activity before it impacts your business, direct intervention capabilities that block fake reviews and prevent malicious edits, and established relationships with Google support that expedite resolution when problems arise. We don't just react to problems—we prevent them.
Key benefits our clients experience include rapid recovery from spam attacks and profile suspensions due to our fast intervention and advocacy with Google support. Businesses routinely see measurable increases in local search visibility, review scores, and conversion rates after implementing our GBP strategy and protection protocols.
For service-based businesses with multiple locations or complex local search needs, we scale GBP best practices while maintaining consistency across all profiles. We resolve bulk suspension issues, create processes for centralized reputation management, and provide the ongoing oversight that busy business owners simply don't have time to manage themselves.
Our value proposition is simple: we blend deep GBP technical expertise with hands-on, proactive reputation and security management, resulting in safer, more visible, and more profitable Google Business Profiles for our clients. Your profile remains compliant, visible, and authoritative in local search results while you focus on running your business.
Frequently asked questions

William Turner
Founder of William & Friends
Hey, I’m William, founder of William & Friends in Denver. We help service businesses get found, get chosen, and get booked. SEO, CRO, and ads tied to clean reporting. Recent wins include 908% year-over-year traffic for a commercial laundry brand and 39% more revenue attributed to organic search for a Denver studio. I write about conversion math, offer-to-channel fit, and operator-grade marketing. If you want the truth about where your pipeline leaks, grab the free marketing audit.
Growth Happens Here
See how our strategies have helped clients dominate their markets:





